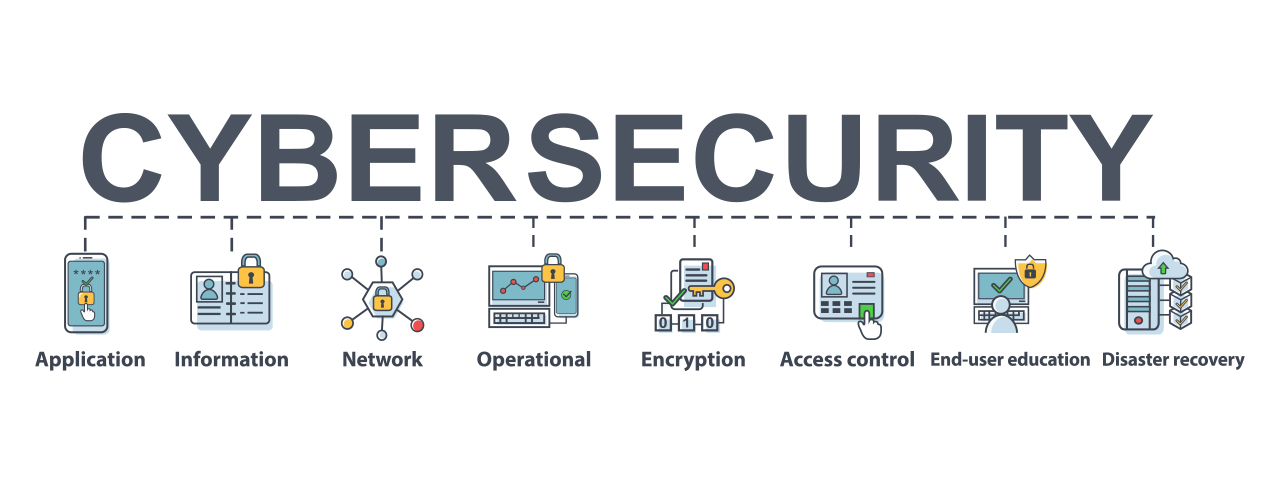
A multi-layer cybersecurity strategy is the very best means to combat any type of serious cyber assault. A mix of firewalls, software program and a range of devices will help battle malware that can impact everything from smart phones to Wi-Fi. Below are several of the means cybersecurity professionals combat the attack of digital assaults.
Cyber Security Consulting Things To Know Before You Buy
VPNs create a safe and secure network, where all information sent out over a Wi-Fi connection is Continue secured.
The smart Trick of Cyber Security Consulting That Nobody is Discussing
Safety made application assistance minimize the risks and also guarantee that Learn More Here when software/networks fall short, they fall short secure (Cyber Security Consulting). Strong input recognition is typically the initial line of protection versus different kinds of injection attacks. Software program and applications are made to approve individual input which opens it as much as assaults as well as right here is where strong input validation helps filter out harmful input hauls that the application would certainly refine.
Something failed. Wait a minute and attempt once again Try once more.